Part two of a three-part series by guest Terry Slattery, CCIE #1026, NetCraftsmen
Part two of a three-part series by guest Terry Slattery, CCIE #1026, NetCraftsmen
In our last article, we talked about the importance of network inventory as a first step in ensuring network consistency and security. In this article, we will talk about how regular network configuration audits contribute to modern network management.
Use Automation, not Manual Verification
When was the last time you verified the correctness of configurations across the entire network? Amazingly, for most organizations, the answer is “never”. Manual methods just don’t work. People get bored and make mistakes. The manual process takes too much time and there are more pressing problems to address. An Intent-Based, automated approach is critical – and easier and more cost-effectively to implement than you might think.
The first step in configuration auditing is to complete a comprehensive network inventory that identifies all network devices including hardware, firmware and software. Network inventory was the subject of the prior article in this series.
Next, an automated mechanism is needed to perform the checks in a reasonable amount of time and to avoid human errors. The automation system is driven by configuration policies that define intent—how you want the network to function.
Some organizations are reluctant to use automation for network configuration. That’s not a problem for configuration backup and configuration audit, which is only reading and comparing configurations against the organization’s defined policies. Configurations are not changed, so there’s no risk of installing a defective configuration. It is also a great way to become familiar with the tools before using them for more complex tasks.
Configuration Backup
Configuration backups are required for business continuity in case of device failure or a more general disaster. It is also the first step to auditing. The command-line interface (CLI) is the most common method and will work across all devices. The management system connects to the device via ssh (preferred) or telnet (insecure) and issues commands to access privileged mode and show the configuration. Some management systems will incorporate either SNMP or API interfaces to retrieve configurations and these methods may allow for either plain text or XML formatting.
Configuration backups must report when a backup fails, allowing the network team to investigate. It could be a temporary problem like device unreachable, or a permanent change like device removal or replacement with a different model. You can then decide whether the failed backup needs further investigation.
Configuration Audit: Discovering Your Source of Truth
Effective configuration audits depend on two things:
- Operating System consistency across all devices of the same type. Command syntax and output can change in subtle ways between releases. Using the same OS across all devices of the same model avoids subtle bugs. OS consistency is achieved through the Inventory and OS update functions (see Inventory: The Foundation for Configuration Management).
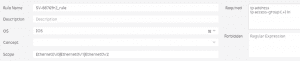
- Standardized configuration policies. Configurations that are based on standardized policies will naturally be consistent. The configuration audit function uses matching rules to validate installed configurations (see the example below). The Gluware Configuration Audit function uses regular expressions to match commands that are either required or forbidden. The Scope defines the extent of the match. Finally, each policy can include multiple rules. The system will identify configuration sections that are not compliant with the policy.
Figure 1: Gluware Policy Rule Editor
Since it is easiest to implement and track, it is recommended to start with simple configurations like SNMP, NTP, and logins. From there, you can proceed to more complex parts of the configuration. The best approach uses simple, independent rules, which are then combined to create more complex policies. These rules and policies become your “source of truth” for network configurations. A policy change will result in a network-wide configuration change that brings the network into compliance with the new policy.
When an exception is detected, you’ll want an easy way to view the non-compliant parts of the configuration. This is another place where ease of use is important. It should indicate whether a required line is missing or a prohibited line has been found.
When a configuration is found to be non-compliant, some systems will include a mechanism that allows you to click a button to remediate the configuration. Only the non-compliant section of the configuration should be modified. The use of the automatic remediation feature implies that you are comfortable with automation for configuration changes.
Using Configuration Audit
A good configuration audit system is easy to use. It automatically performs configuration backup from any supported devices. The configuration rule/policy editor should be easy-to-use for both simple and complex policies. Both scheduled and ad-hoc policy checks are necessary. Scheduled checks look for devices that are not in compliance with the policy. Ad-hoc checks allow you to easily answer questions about which devices contain a given configuration. This latter function is great for determining security vulnerabilities based on a specific configuration.
While the audit functionality allows you to identify changes, the real power comes from the system’s ability to make configuration changes. You may wish to verify the system’s recommendations by making the changes manually for a while. Once you’re comfortable that it is taking the correct actions, trigger it to update a test device. Then transition to a relatively less important production device. Test the configuration update mechanism with different sized groups of devices, starting with one device per group and increasing the group size as the system proves itself. You’re also looking for an indication of how long it takes each group to be processed.
Gluware’s Configuration Audit Capability
The Gluware Intelligent Network Automation platform performs all the functions described in this article. It automatically captures and stores device configurations. The configuration policy system is based on simple rules that can be combined together to form more complex policies without the need to learn programming. (Note: You will need to know regular expressions for most any system.) Like any configuration audit system, you can need to spend some time learning how it works and how to best apply it to your network. You should expect to spend the majority of your time making the operating systems and configurations consistent. The result will be a network that is much easier to manage and has fewer problems. That makes it worth doing.
Interested in learning more?
Watch the video demonstration of the Gluware Config Drift and Audit
Try Gluware for yourself – Request a Test Drive